Edgenexus ALB-X Lync 2010 & 2013 Deployment Guide
Synopsis
Overview
Pre-requisites
Why
Edgenexus?
LAB
Environment
Lync 2010/2013 Description
What
server role can be load balanced by Edgenexus ALB-X?
Standard Lync Deployment
Configuring
External Edge Pool
Configuring
Internal Edge Pool
Configuring Reverse
Proxy
jetPACK Quick Installation
Troubleshooting
Contact
Us
Synopsis
This online guide explains briefly the concept of
Lync 2010/2013 and how
to use a Edgenexus Accelerating Load Balancer (ALB-X) to load balance
Lync 2010/2013
traffic.
Overview
Microsoft
Lync (previously known as Microsoft
Office Communications Server) is a real-time communications server for
the
enterprise. In response to today’s changing working patterns and the
need for
real-time collaboration, organisations are looking for integrated
productivity
tools that enable users to communicate from anywhere in a
cost-effective and
secure manner.
As with any service-oriented architecture, it is essential that
applications
run seamlessly with superb performance and robust security. The nature
of
Lync’s real-time communication and collaboration services, together
with its
business critical importance demands a high level of service delivery.
Enter
Edgenexus – Application Delivery Control
for Microsoft Lync
The
Edgenexus Accelerating Load Balancer is
specifically developed to improve the performance, scalability,
reliability and
manageability of Microsoft Lync. Easy to deploy, configure and
maintain, the Edgenexus ALB-X for Lync has the simplicity of a
plug-and-play solution, with the performance capabilities to meet even
the most demanding traffic profiles.
Pre-requisites
The following are general prerequisites and
configuration
notes for this guide:
-
- It is assumed that the reader is a
network administrator or person familiar with networking and general
computer terminology
- It is assumed that the reader is a
-
- You have set-up your Microsoft Lync
Enterprise Server 2010 environment and have installed your Edgenexus
ALB-X application delivery controller
- You have set-up your Microsoft Lync
-
- You have configured your internal and
external DNS entries for the Front-End and Edge Pools, and services accessed by Reverse Proxy
- You have configured your internal and
- When Microsoft refer to a hardware
load balancer (HLB) it is equivalent to the industry term “Application
Delivery Controller” - You are running Software Version 4.0.1 (Build 1576) or later on you Edgenexus ALB-X
Webscheduler
It is advised to create a simple url for webscheduler. This url should map to the same external internet facing IP as meet and dialin.
E.g. you can go to https://ReverseProxyWebfqdnOfPool/scheduler where ReverseProxyWebfqdnOfPool has a separate external internal facing IP or
you can create DNS SRV records and forwarding rules for your external interface for external user signin without autodiscover and federation traffic.
For further details refer to https://technet.microsoft.com/en-us/library/gg412787.aspx
For user sign-in: _sip._tls.
-> your edge external interface FQDN.
For federation: _sipfederationtls._tcp.
-> your edge external interface FQDN.
Why Edgenexus?
| Server Health Monitoring | Application layer server health checks, detect and route around problems to eliminate downtime |
|
| Layer 4 & Layer 7 Load Balancing |
Speedy layer 4 load balancing with layer 7 health checks ensure the most efficient load balancing is acheived | |
| Reverse Proxy | Traffic from external clients is securely proxied by Edgenexus ensuring no external client can directly access internal resources | |
| Session persistence | Edgenexus Lync Reverse Proxy uses specifically named cookies to provide session persistence to the Front End pool | |
| Compression | Compression is automatically used to accelerate external web and mobile clients | |
| SSL Re-encryption | Enables end to end secure encrypted traffic between client and internal resources whilst still being able to provide acceleration and traffic manipulation with flightPATH |
|
| flightPATH | Our intelligent application layer traffic manipulation engine can be easily configured to redirect web and mobile clients to the correct services |
LAB Environment
This
Guide for Load balancing Microsoft Lync 2010/2013 has been designed on
the following configuration.
-
Lync
2010
- An Enterprise Front End pool, consisting of two
nodes. Consolidating Conferencing, Enterprise Voice and Mediation
Server features
- Each Front End server was configured on a
Microsoft Windows 2008 R2 Server with a single NIC, on a private IP
address. Each NIC has a single IP address.
- An Edge pool, consisting of two nodes.
Consolidating SIP, Web Conferencing and A/V services. Each of these
services is configured using a common IP/Hostname and different ports
for each service - Each Edge server is configured on a Microsoft
Windows 2008 R2 Server with two NICs. One on the Private LAN, and
another on a DMZ LAN. Each NIC has a single IP address, and the DMZ NIC
is configured with a default gateway - A single Database Server, configured on a
Microsoft Windows 2008 R2 Server running Microsoft SQL 2008 R2
-
Lync
2013
- An Enterprise Front End pool, consisting of two nodes.
Consolidating Conferencing, Enterprise Voice and Mediation Server
features - Each Front End server
was
configured on a Microsoft Windows 2012 Server with a single NIC, on a
private IP address. Each NIC has a single IP address. - An Edge pool,
consisting of two nodes. Consolidating SIP, Web Conferencing and A/V
services. Each of these services is configured using a common
IP/Hostname and different ports for each service - Each Edge server is
configured on a Microsoft Windows 2012 Server with two NICs. One on the
Private LAN, and another on a DMZ LAN. Each NIC has a single IP
address, and the DMZ NIC is configured with a default gateway - A single
Database Server, configured on a Microsoft Windows 2012 Server running
Microsoft SQL 2012
Common to Lync 2010 & 2013
- A single PSTN Gateway
running a configured SIP trunk
- A Single File Store, a
simple file share available on the Private LAN
- No Director, Archiving
or Monitoring Servers were configured
M
Lync 2010/2013 Description
Server Roles
The Front End Server
services to a common group of users.
address book services
Directors
home user accounts or provide presence or conferencing services.
Directors are most useful to enhance security in deployments that
enable external user access. The Director can authenticate requests
before sending them on to internal servers. In the case of a
denial-of-service attack, the attack ends with the Director and does
not reach the Front End servers
Mediation Server
voice conferencing. This role processes and translates different VOIP
codecs. If you already have an existing VOIP system, you will be
running a SIP trunk to your VOIP system. This can be collocated with
the Front End server role.
A/V Conferencing Server
be installed as a single role or with the Front End server.
Edge Server
it’s a proxy between internal and external clients. This role allows
Lync clients to communicate with users outside company firewalls, which
includes external users that may not have an account in your company’s
Active directory.
Archiving and Monitoring
conversations, Group Chat and conference logs.
What server role can be load balanced
by Edgenexus ALB-X?
Front End Pool
balance the traffic
Director Pool
load balance the traffic
Mediation Pool
Edge Pool
balance the traffic
Reverse Proxy
to HTTPs and port address translate 443 to 4443 necessary for External
Web Services
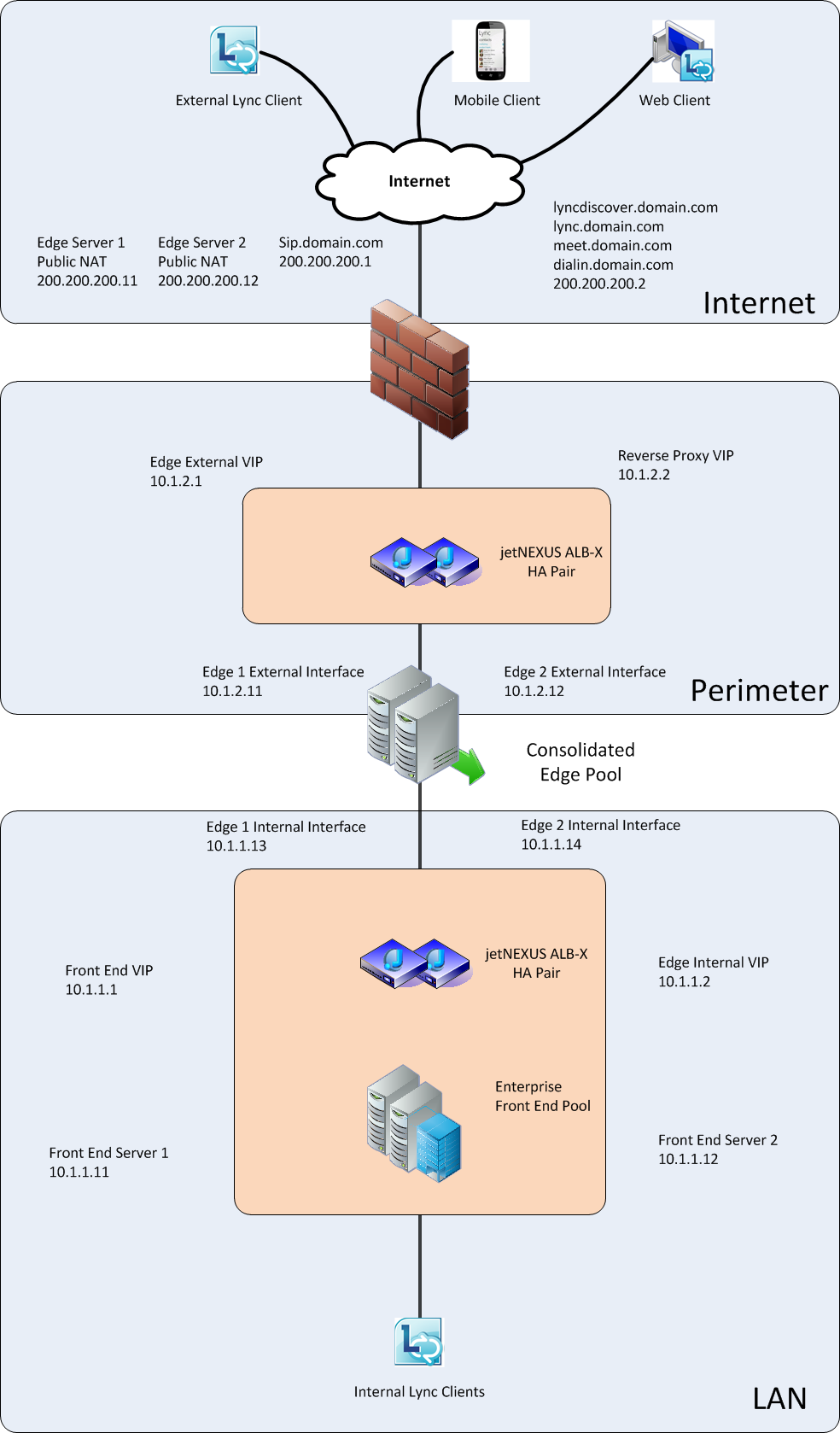
Standard Lync Deployment
Diagram 1.1
Configuring the FrontEnd Pool
Required Services
for the Front End Pool: – Table 1.1
|
Service Name |
Port |
Service Type |
Connectivity |
Health Check |
Persistence |
Notes |
|
FE |
135 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
RPC/DCOM |
|
FE |
5061 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
SIP/TLS |
|
FE |
5065 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Application |
|
FE |
5069 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
QoE |
|
FE |
444 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Conferencing |
|
FE |
443 |
Layer4 TCP |
Reverse Proxy | TCP Connect |
IP Bound |
HTTPS |
|
FE |
4443 |
HTTP |
Reverse Proxy |
Lync |
Cookie |
HTTPS |
Optional
Services for Front End Pool: – Table 1.2
|
Service Name |
Port |
Service Type |
Connectivity |
Health Check |
Persistence |
Notes |
|
FE |
80 |
Layer4 TCP |
Reverse Proxy |
200OK |
IP Bound |
HTTP |
|
FE |
8080 |
Layer4 TCP |
Reverse Proxy |
200OK |
IP Bound |
HTTP |
|
FE |
448 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Call |
|
FE |
5060 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
SIP |
|
FE |
5067 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Mediation |
|
FE |
5068 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Mediation |
|
FE |
5070 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Mediation |
|
FE |
5071 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Response |
|
FE |
5072 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Conferencing |
|
FE |
5073 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Conferencing |
|
FE |
5074 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Outside |
|
FE |
5075 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Call |
|
FE |
5076 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Call |
|
FE |
5080 |
Layer4 TCP |
Reverse Proxy |
TCP |
IP |
Call |
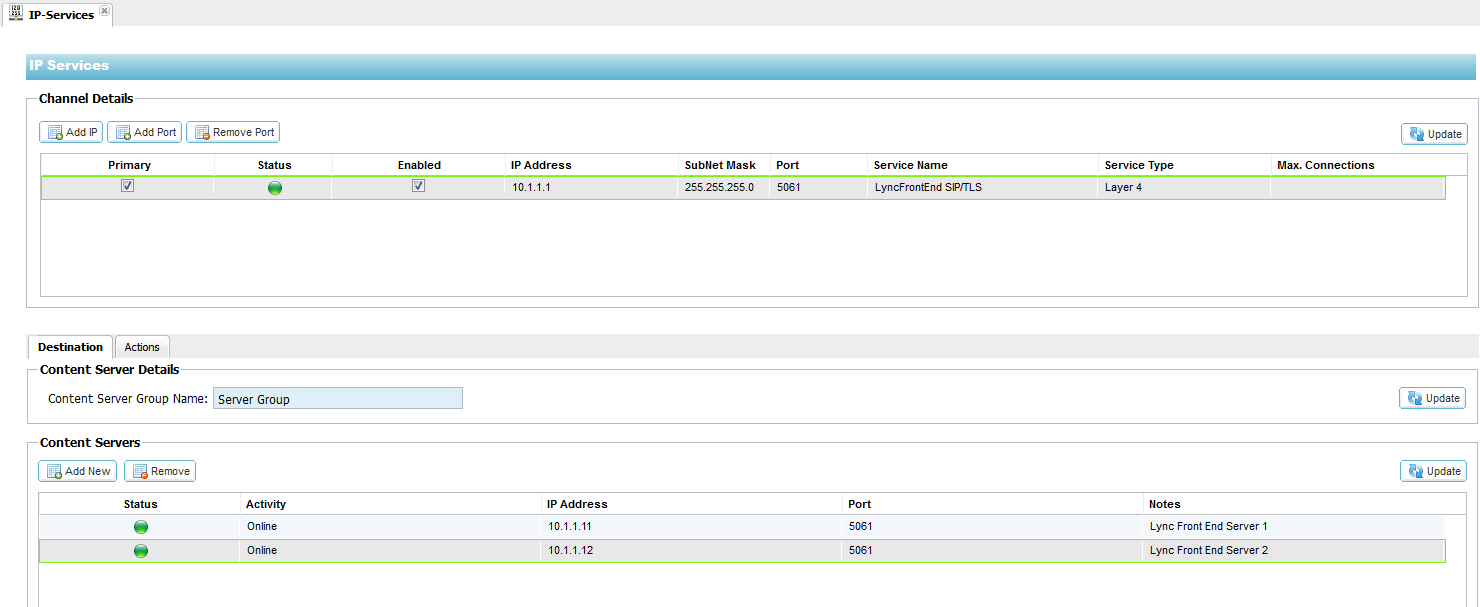
Configuring a
Virtual Service for SIP services on the Lync-Front-End Pool
1. Log on to your Edgenexus ALB-X https://x.x.x.x and open up the IP-Services page
2. Click Add IP and complete each column with the
details below taking care to replace the IP addresses here with your
own.
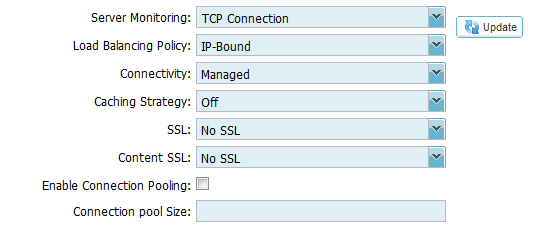
3. Click on the Actions – Basic Tab and set each
setting as below
4. Click on the Actions – Advanced Tab and set each
setting as below
Configuring a Virtual Service for Additional SIP services on
the Front-End Servers
1. Log on to your Edgenexus ALB-X https://x.x.x.x and open up the IP-Services page
2. Click Add Port and complete the columns as
per Table 1.1 & 1.2 as required for your deployment
3. The Actions-Basic settings should be configured
the same for all SIP based services
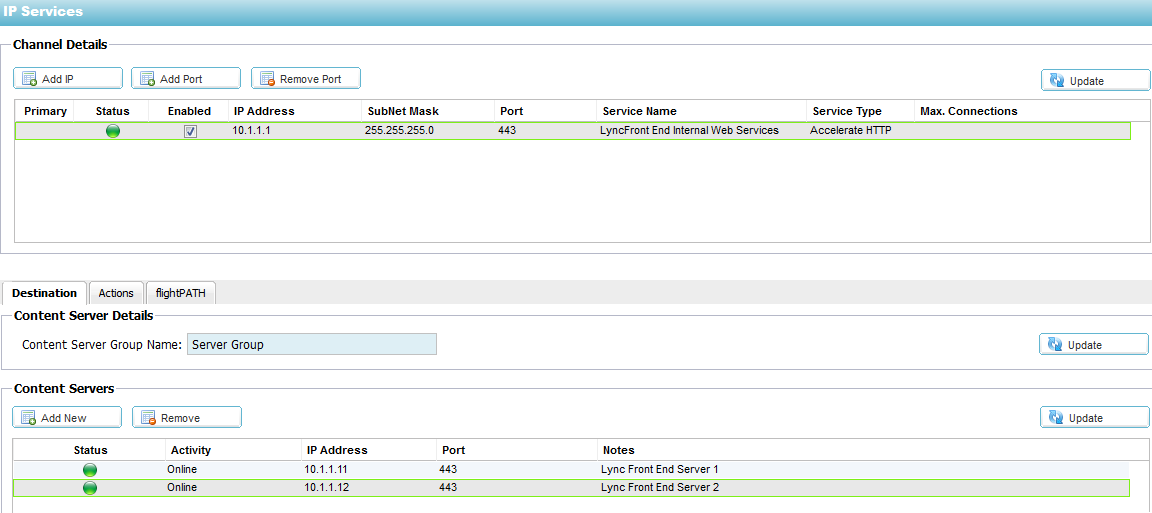
Configuring a Virtual Service for Internal HTTPS-based services for the Front-End servers
1. Log on to your Edgenexus ALB-X https://x.x.x.x and open up the IP-Services page
2. Click Add IP and complete each column with the
details below taking care to replace the IP addresses here with your
own.
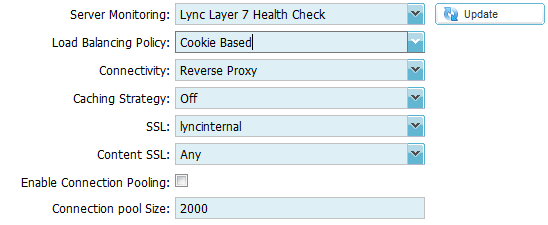
3. Click on the Actions – Basic Tab and set each
setting as below
4. Click on the Actions – Advanced Tab and set each
setting as below
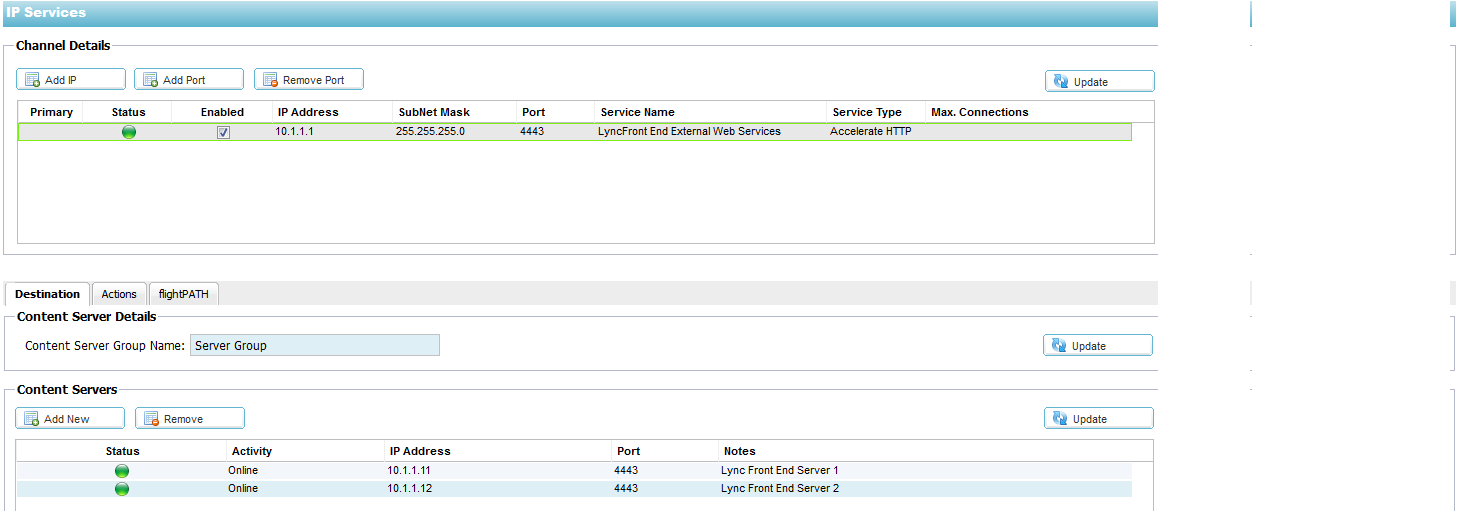
Configuring a Virtual Service for External HTTPS-based services for
the Front-End servers
1. Log on to your Edgenexus ALB-X https://x.x.x.x and open up the IP-Services page
2. Click Add IP and complete each column with the
details below taking care to replace the IP addresses here with your
own.
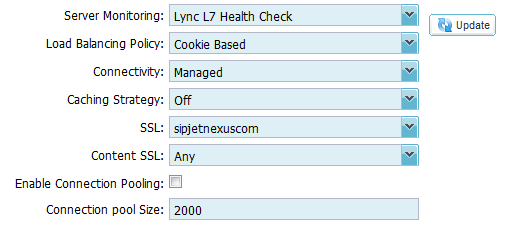
3. Click on the Actions – Basic Tab and set each
setting as below
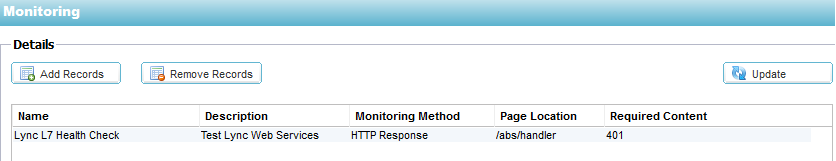
4. The “Lync Layer 7 Health Check” is configured in
the Configure – Real Server Monitor section
5. The Cookie name must be set to MS-WSMAN. Please
contact pre-sales@edgenexus.io for the Lync 2010 Cookie jetPACK which
will change this setting automatically
6. The SSL Certificate must be the same certificate
on the Front End Servers and is typically your public certificate with subject alternative names
Import this certificate onto the Edgenexus ALB-X – for details on this please see https://appstore.edgenexus.io/user-guides/user-guide-4-1-4/software-version-4-1-4-user-guide/ssl-certificates/
The certificate will now be available to choose from the drop down list in the SSL section. Our example above shows “sipjetnexuscom” which is a friendly name for our external certificate
7. Content SSL must be set to Any for SSL Bridging also known as SSL Re-Encryption
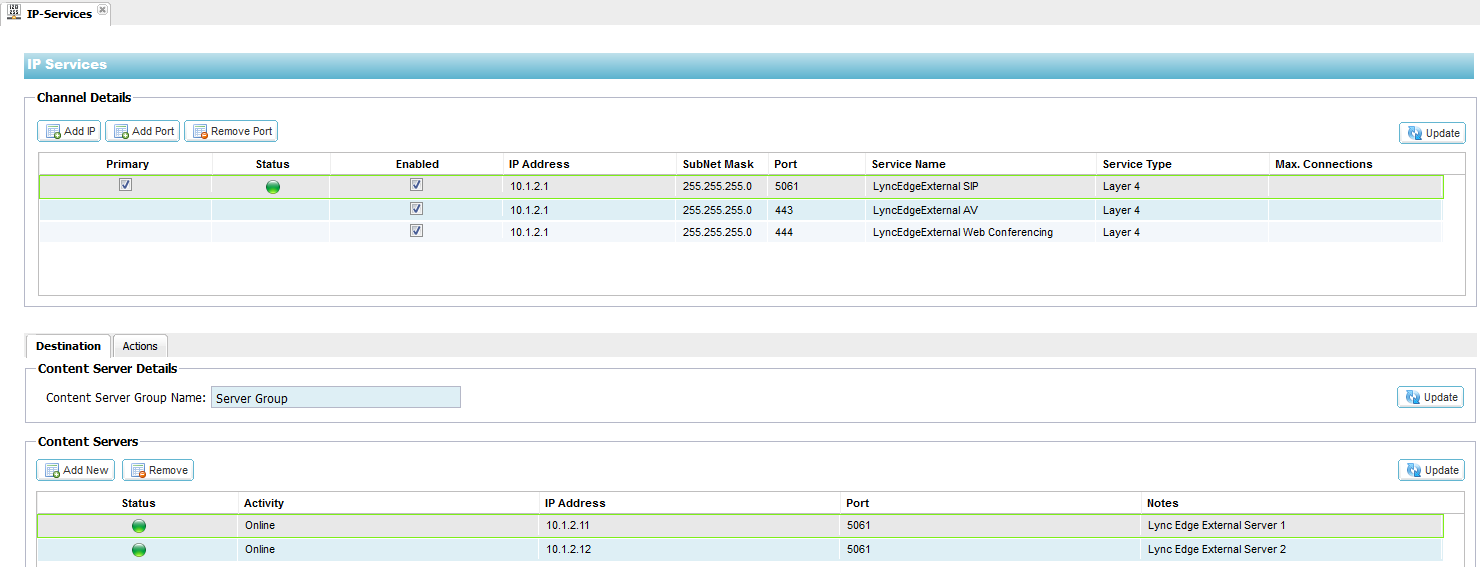
Configuring the Edge Pool
External Interface
1. Log on to your Edgenexus ALB-X https://x.x.x.x and open up the IP Services page
2. Click Add IP and complete each column with the
details below taking care to replace the IP addresses here with your
own.
3. Click on the Actions – Basic Tab and set each
setting as below
4. In this instance we have one Public IP address 200.200.200.1 for
sip.domain.com which will be forwarded to Edgenexus ALB-X Channel IP of
10.1.2.1 and the three services SIP, AV and Conferencing are split by
port consistent with a Lync Consolidated Edge Topology
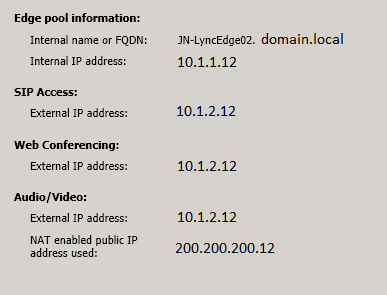
5. Each Edge Server will need a Public IP address and
here we have given Edge Server2 the Public IP address 200.200.200.12.
Where Public IP is an internet routable IP address
6. You will then need to create a one to one NAT for
this public IP address to the External IP address of each Edge Server.
Where External IP is the private IP address of the External interface
of the Edge server. In this instance the External Interface IP address
of Edge Server 2 is 10.1.2.12
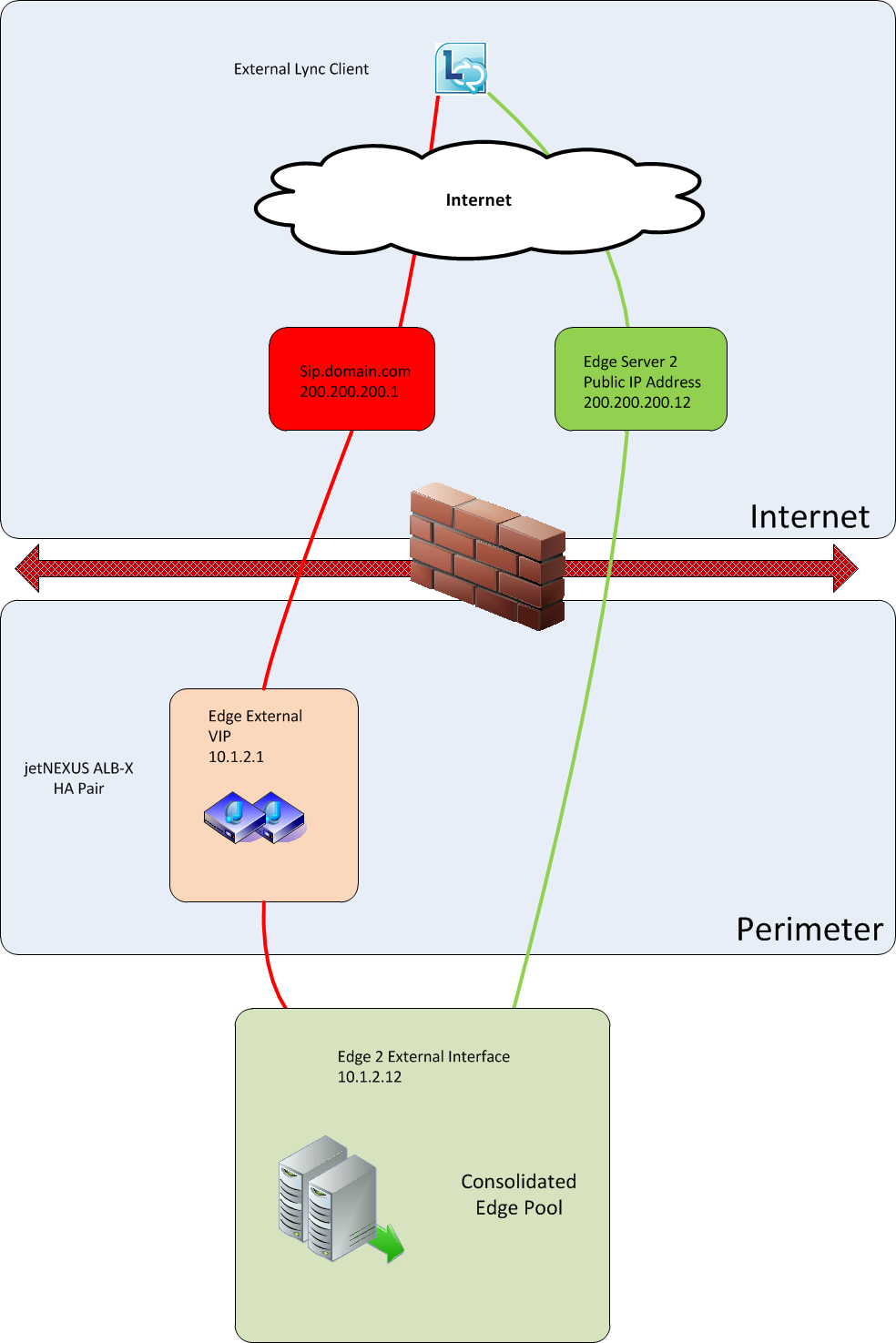
7. The External Lync Client makes an initial
connection to sip.domain.com which is then forwarded to the Edgenexus
VIP and load balanced to the external interface of one of the Edge
Servers
8. The Edge server responds to the client via the
load balancer with its Public IP address 200.200.200.12
- 9.
The Lync Client then connects direct with the Edge Server’s public
address
10. Ensure you have the correct firewall rules for
the Edge Server ports. http://technet.microsoft.com/en-us/library/gg425882.aspx
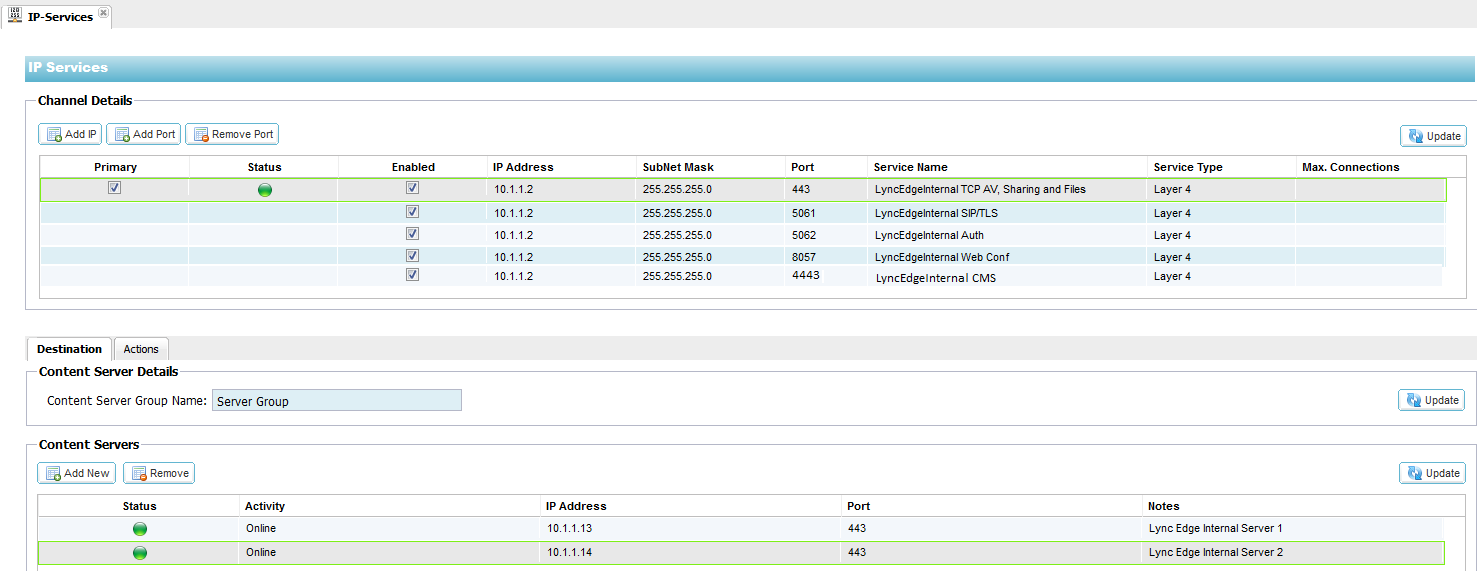
Edge Internal Interface
-
- 1. Log on to your
Edgenexus ALB-X https://x.x.x.x and open up the IP Services page
- 1. Log on to your
2. Click Add IP and complete each column with the
details below taking care to replace the IP addresses here with your
own.
3. Click on the Actions – Basic Tab and set each
setting as below
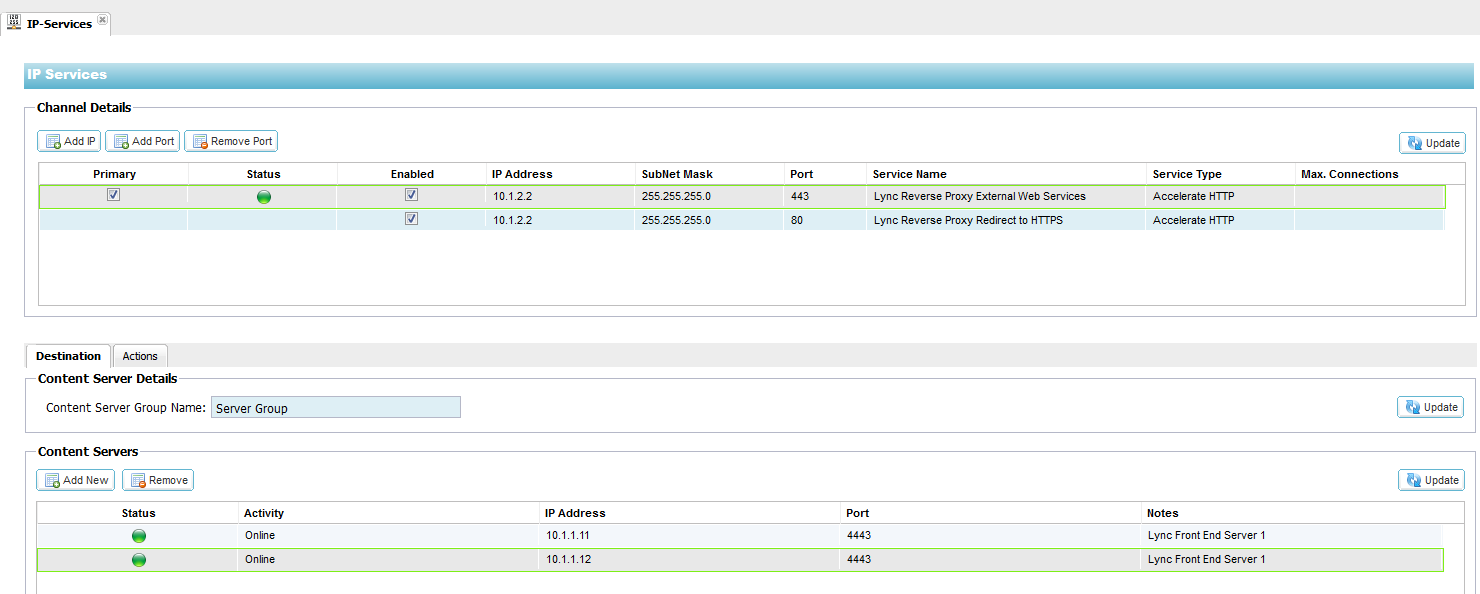
Configuring the ALB-X as a Reverse
Proxy
- 1. Log on to your Edgenexus
ALB-X https://x.x.x.x and
open up the IP Services page
2. Click Add IP and complete each column with the
details below taking care to replace the IP addresses here with your
own.
3. Notice on the 443 Channel we have port address
translated to 4443 to the Lync Front End Servers. Now Click for the 443
channel on the Actions – Basic Tab and set each setting as below
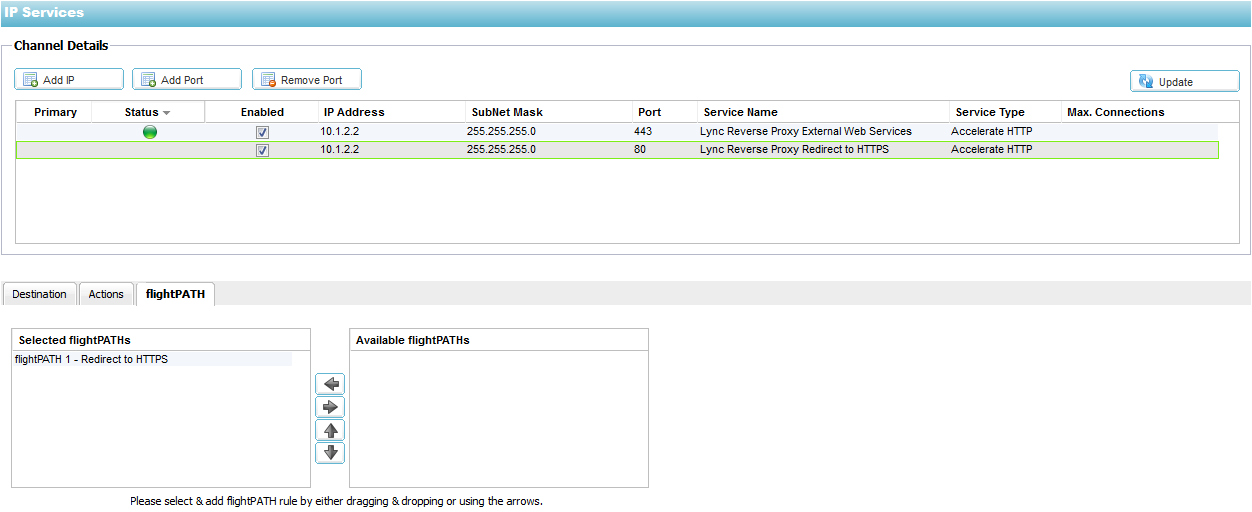
4. The recommended policy is to run a flightPATH rule
on the HTTP port 80 channel to redirect all traffic to the secure HTTPS
443 channel.
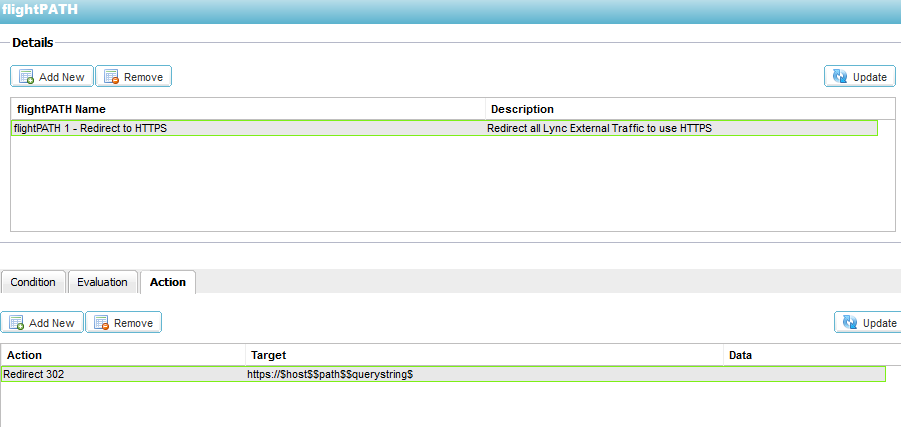
5. The flightPATH rule flightPATH 1 – Redirect to HTTPS is configured in
the Configure—flightPATH section as below. The Condition and Evaluation should be left blank and the Action is detailed below
jetPACK Quick Installation
| The Edgenexus ALB-X can be configured automatically with a Lync 2010/2013 “jetPACK”, template which is fully-tuned with all of the application-specific settings that you need in order to enjoy optimised service delivery from your ALB-X |
||
| If you supply the virtual IP address and real server IP addresses to support@edgenexus.io we will send you a custom jetPACK that you simply upload to the Edgenexus ALB-X |
||
| The upload can be done via the GUI and will be fully configured in less than 1 minute |
||
| The relevant jetPACK can be applied to multiple Edgenexus ALB-X appliances saving valuable time and eliminating simple mistakes |
||
| For more information and to download a jetPACK please go to our website https://appstore.edgenexus.io/jetpack-2/#Microsoft_Lync |
Troubleshooting
Further help can be found on the main Edgenexus website
http://www.edgenexus.io/support/
User central
Contact Us
I hope you have found this Deployment Guide informative, but if you
need any clarification or further information, please do not hesitate
to get in contact with edgeNEXUS Support:
|
|
support@jetNEXUS.com |
Phone |
+44 (0870) 382 5529 |
Blog |
http://jetNEXUS.blogspot.com/ |
 Back to Top
Back to Top