Authentication
The Library — Authentication page allows you to setup authentication servers and create
authentication rules with options for client side
Basic or Forms and for server side NTLM or BASIC.
The page is organised into the section below.
Work Flow
Please carry out the following steps as a minimum to apply Authentication to your service.
- Create an Authentication Server.
- Create an Authentication Rule that uses an Authentication Server.
- Create a flightPATH rule that uses an Authentication Rule.
- Apply the flightPATH rule to a Service.
Authentication Servers
First we must create a server to authenticate against.
- Click Add Server
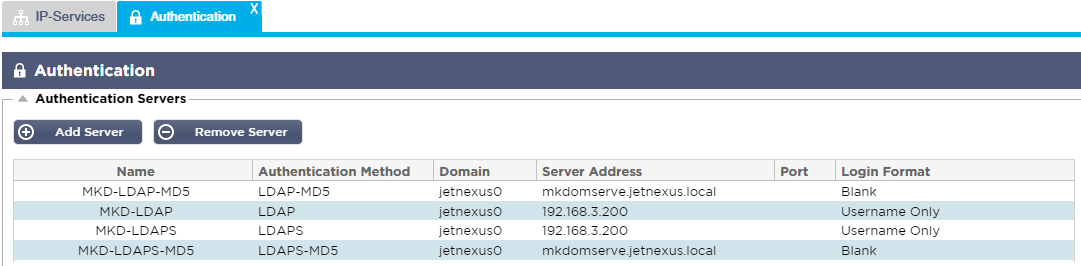
- This will produce a blank row ready for completion.
- Name – give your server a name for identification purposes – this name will be used in the rules below.
- Description – add a description.
- Authentication Method – choose an authentication method.
- LDAP – basic LDAP with usernames and passwords sent in the clear to the LDAP server.
- LDAP-MD5 basic LDAP with username in the clear but password MD5 hashed for increased security.
- LDAPS – LDAP over SSL. The password is sent in the clear but within an encrypted tunnel between the ALB-X and the LDAP server.
- LDAPS-MD5
– LDAP over SSL. The password is MD5 hashed for added security within
an encrypted tunnel between the ALB-X and the LDAP server.
- Domain – add in the domain name for the LDAP server.
- Server Address:
- LDAP – IPv4 address or hostname.
- LDAP-MD5 – hostname only (IPv4 address will not work).
- LDAPS – IPv4 address or hostname.
- LDAPS-MD5 – hostname only (IPv4 address will not work).
- Port – this
will use port 389 for LDAP and port 636 for LDAPS by default. No need
to add the port number for LDAP and LDAPS. When other methods become
available you will be able to configure it here. - Search Conditions – these search conditions must conform to RFC 4515. Example: (MemberOf=CN=Phone-VPN,CN=Users,DC=jetnexus,DC=local).
- Search Base – Starting point for the search in LDAP database. Example dc=jetnexus,dc=local.
- Login Format:
- Username – when
this format has been chosen you need only enter the username. Any
user domain information entered by the user will be deleted and the
domain information from the server will be used. - Username and Domain – The
user must enter the full domain and username syntax. Example:
jetnexus\gchristie OR gchristie@jetnexus. The domain information
entered at the server level will be ignored. - Blank – we will accept anything the user inputs and send on to the authentication server. This must be used when using MD5.
- Username – when
- Passphrase – Not used in this version.
- Dead Time – Not used in this version.
Authentication Rules
Now we can create a rule that will use the server we created above.
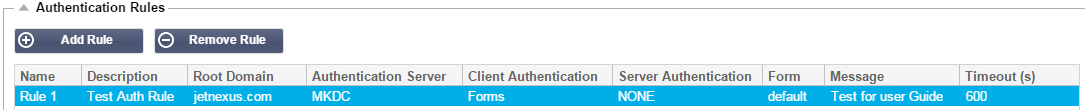
- Name: add a suitable name for your authentication rule.
- Description: add suitable description.
- Root Domain: This must be left blank unless you need single-sign-on across sub-domains.
- Authentication Server: this is a drop down box that will contain any servers taht you have configured.
- Client Authentication:
- Forms
– this will present the edgeNEXUS default form to the user. Within the
form you can add a message. You can select any other form that you
have uploaded using the section below. - own pop-up to allow a user logon
to your service. Note that the timeout value will be ignored for
Basic Client Authentication.
- Forms
- Server Authentication Basic (401)
– the browser will present its:- None
– if your server does not have any existing authentication select
this setting. This means that you can now add authentication to a
server that previously had none. - Basic – if your server has basic authentication enabled then select BASIC.
- NTLM – if your server has NTLM authentication enabled then select NTLM.
- None
- Form:
- Default – this is the default edgeNEXUS form.
- Custom – you can add your own form with your own name and select it here.
- Message: add a message to the form.
- Timeout: add
a timeout to the rule after which the user will be required to
authenticate again. Note this is only valid for Forms based
authentication.
Single Sign On:
If you wish to provide a single sign on for users simply complete the Root Domain column with your domain.
In
this example we have used jetnexus.com. We can now have multiple
services that will use the jetnexus.com as the root domain and you will
only have to login once.
If we consider the following services:
- sharepoint,jetnexus.com
- usercentral.jetnexus.com
- appstore.jetnexus.com
These services can reside on one VIP or can be distributed across 3 VIPs.
A
user accessing usercentral.jetnexus.com for the first time will be
presented with a form asking them to log in depending on the
authentication rule used.
The same user then access appstore.jetnexus.com and will be authenticated automatically by the ALB-X.
You can set the timeout which will force authentication once this period of in-activity has been reached.
Forms
This section will enable you to upload a custom form.
Creating your own form
In you wish to create your own custom form please use the following details within your htm or html form.
- Name of your form:
- form name = loginform
- action = %JNURL%
- Method = POST
- Username:
- name = “JNUSER”
- Password:
- name=”JNPASS”
- Optional Message1:
- %JNMESSAGE%
- Optional Message2:
- %JNAUTHMESSAGE%
- Images
- If you wish to add an image then please add it in-line using Base64 encoding.
Example html of simple form
| <HTML> | |
| <HEAD> | |
| <TITLE>SAMPLE AUTH FORM</TITLE> | |
| </HEAD> | |
| <BODY> | |
| %JNMESSAGE%<br> | |
| <form name=”loginform” action=”%JNURL%” method=”post“> | |
| USER: <input type=”text” name=”JNUSER” size=”20” value=””></br> | |
| PASS: <input type=”password” name=”JNPASS” size=”20” value=””></br> | |
| <input type=”submit” name=”submit” value=”OK“> | |
| </form> | |
| </BODY> |
Example screen shot of default form

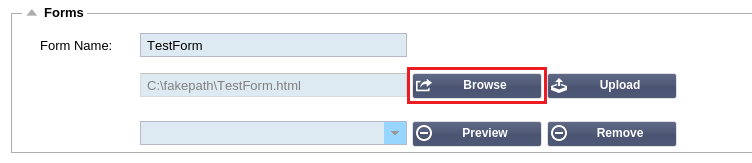
Adding a custom form
Once you have created a custom form you can add it using the Forms section.
- Choose a name for your form
- Browse locally for your form
- Click Upload
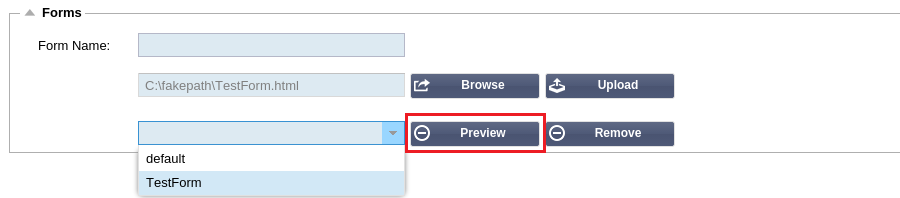
Preview a custom form
To view the custom form you have just added simply select it and click preview.
You may also use this section to delete forms that are no longer required
flightPATH
The final bit to tie everything together is to create a flightPATH rule and apply it to a Virtual Service
- Navigate to Library–flightPATH
- In the details section click Add New
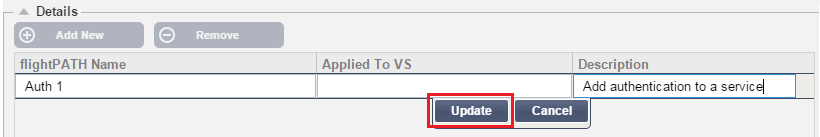
- Enter a name for your rule. Example Auth2
- Enter a description of your rule
- Once the rule has been applied to a service you will see the Applied To column auto populate with an IP address:Port
- Don’t forget to hit update to save your changes or if you make a mistake just hit cancel to remove all changes
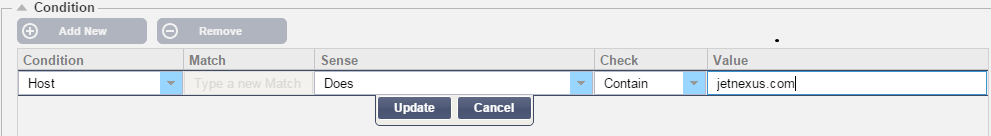
- Next we need to Add New Condition
- Choose a condition from the drop down box. Example Host
- Choose a Sense. Example Does
- Choose a Check. Example Contain
- Choose a Value. Example jetnexus.com
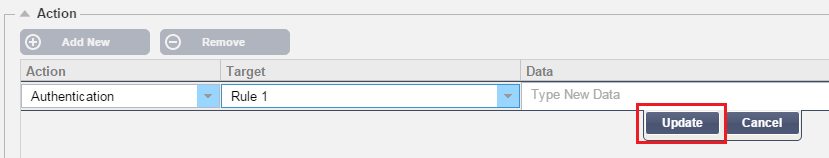
- Now we need to add an action to our rule
- Click Add New
- Choose Authentication from the drop down
- Choose the rule created within the Authentication page. Example Rule 1
- Click Update
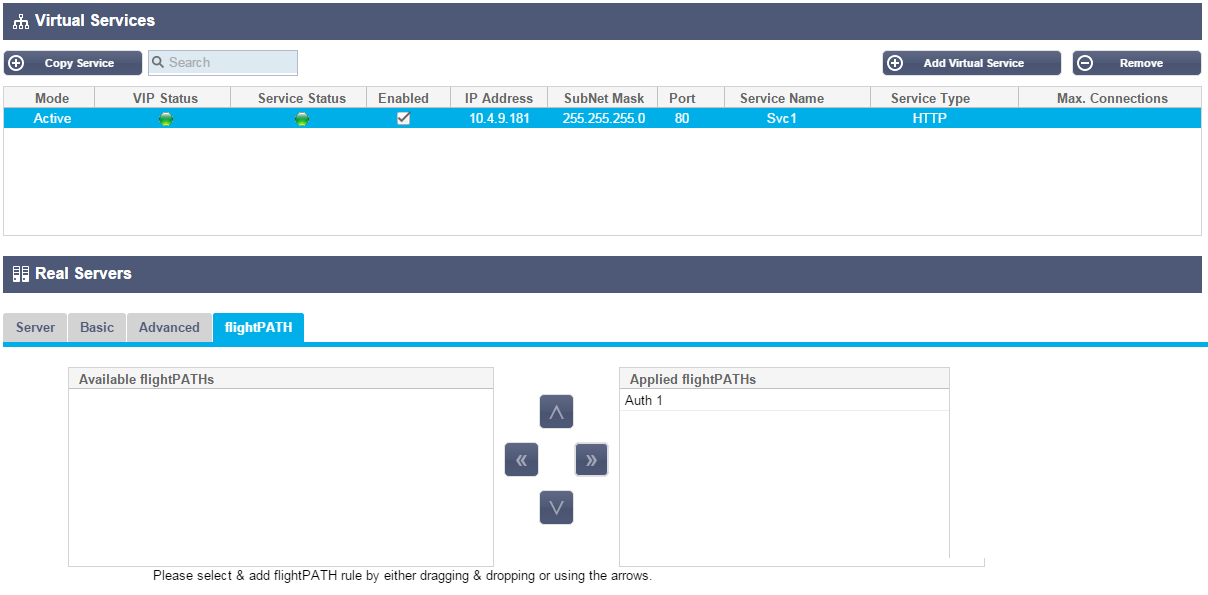
Finally we need to apply this flightPATH rule to a virtual service
- Navigate to Services–IP Services
- Highlight the desired Virtual Service
- Click on the flightPATH tab
- Select the rule from the Available flightPATHs. Example Auth1
- Click the right arrow or drag the rule to the Applied flightPATHs
 Back to Top
Back to Top