Network
The Library—>Network
configuration page allows you to view and update the routing information on the jetNEXUS ALB-X. The settings are organised in the following sections:
Basic Setup
Basic Setup:
ALB Name:
Add in a name for your jetNEXUS ALB-X appliance. Please note that this cannot be changed if there is more than 1 member in the Cluster. Please see
ClusteringIPv4 Gateway:
Add in the IPv4 Gateway address.This will need to be in the same subnet as an existing adapter. If you add in Gateway incorrectly you will see a White Cross in a red circle. When you add in a correct gateway you will see a green success banner at the bottom of the page and a white tick in a green circle next to the IP address.
IPv6 Gateway:
Add in the IPv6 Gateway address. This will need to be in the same subnet as an existing adapter. If you add in Gateway incorrectly you will see a White Cross in a red circle. When you add in a correct gateway you will see a green success banner at the bottom of the page and a white tick in a green circle next to the IP address.
DNS Server 1:
Add in the IPv4 address of your first DNS server.
DNS Server 2:
Add in the IPv4 address of your second DNS server
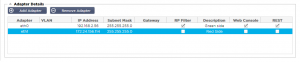
Adapter Details
Here you can add, remove and update the adapter settings.
Adapter:
Double click to see the physical adapters installed on your appliance. Choose an adapter from the list
VLAN:
Double click to add the VLAN ID for the adapter. A VLAN is a Virtual Local Area Network which creates a distinct broadcast domain. A VLAN has the same attributes as physical LAN but it allows for end stations to be grouped together more easily if they are not on the same network switch
IP Address:
Double click to add the IP address associated with the adapter interface.You can add multiple IP addresses to the same interface. This should be an IPv4 32-bit number in quad dotted decimal notation.
Example: 192.168.101.2
Subnet Mask:
Double click to add the subnet mask assigned to the adapter interface. This should be an IPv4 32-bit number in quad dotted decimal notation.
Example: 255.255.255.0
Gateway:
Add a gateway for the interface. When this is added the ALB-X will set-up a simple policy that will allow connections initiated from this interface to be returned via this interface to the gateway router specified. This allows the ALB-X to be installed in more complex networking environments without the hassle of manually configuring complex policy based routing.
Reverse Path Filter:
This controls the scope by which data can be returned to the client using an asymmertic route. Tick the checkbox to enable reverse-path filtering. This prevents data being routed in complex ways, allowing only symmetric routes. This is a modern higher security configuration. Un-tick the checkbox to disable reverse-path filtering. This allows data to be being routed using asymmetric routes. This is a lower security configuration in a manner compatible with the way older operating systems used to work.
Description:
Double click to add a description for your adapter. Example: Public Interface. Note: The ALB-X will automatically name the first interface Green Side, the second interface Red Side and the third interface Side 3 etc. Please feel free to change these naming conventions to your own choice.
Web Console:
Double click the column then tick the box to assign the interface as the management address for the Graphical User Interface Web Console.Please be very careful when changing the interface that Web Console will listen on. You will need to have the correct routing set up or be in the same subnet as the new interface in order to reach the Web Console after the change. The only way to change this back is to access the command line and issue the set greenside command. This will delete all interfaces except for eth0.
Interfaces
- The settings on this screen control the network access. The defaults are to fix speed at 100 Mbps and full duplex. This avoids any issue with certain networking devices that have auto-negotiation which re-negotiates too frequently.
- The appliance can support speeds from 10 to 1000; for 1000 this should set to auto/auto. If this does not work, set the exact network hardware values.
- The speed and duplex setting should only be changed for hardware appliance.
- Virtual appliances will take their configuration from the underlying hypervisor.
- In this section you can add and remove interfaces to a Bond once the bond has been configured in the section below.
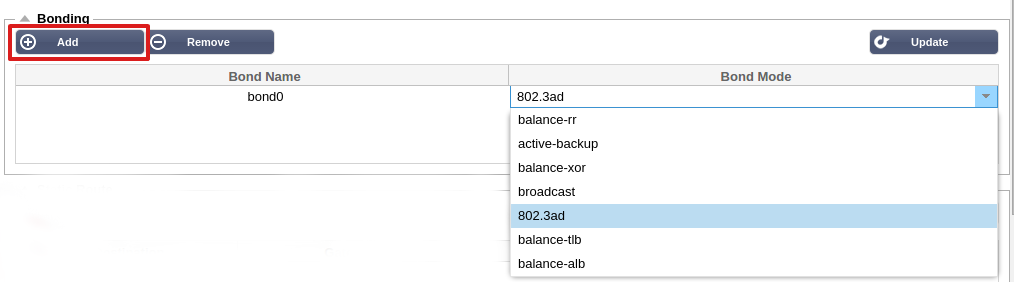
Bonding
Bonding allows you to aggregate multiple ports into a single group, effectively combining the bandwidth into a single connection. Bonding also allows you to create multi-gigabit pipes to transport traffic through the highest traffic areas of your network. Note: this is only
relevant for your hardware version of ALB-X. Do not use bonding for the Virtual Appliance.
Bonding Modes
balance-rr:
Transmits packets in sequential order from the first available slave to the last.
active-backup:
Has one interface which will be active and the second interface will be in standby. This secondary interface only becomes active if the active connection on the first interface
fails.
balance-xor:
Transmits
based on source MAC address XOR’d with destination MAC address. This selects the same slave for each destination Mac address.
broadcast:
Transmits everything on all slave interfaces.
802.3ad:
Creates aggregation groups that share the same speed and duplex settings.Utilizes all slaves in the active aggregator according to the 802.3ad specification.
balance-tlb:
The Adaptive transmit load balancing bonding mode: Provides channel bonding that does not require any special switch support. The outgoing traffic is distributed according to the current load (computed relative to the speed) on each slave.Incoming traffic is received by the current slave. If the receiving slave fails, another slave takes over the MAC address of the failed receiving slave.
balance-alb:
The Adaptive load balancing bonding mode: also includes balance-tlb plus receive load balancing (rlb) for IPV4 traffic, and does not require any special switch support. The receive load balancing is achieved by ARP negotiation. The bonding driver intercepts the ARP Replies sent by the local system on their way out and overwrites the source hardware address with the unique hardware address of one of the slaves in the bond, such that different peers use different hardware addresses for the server.
Configure Bonding
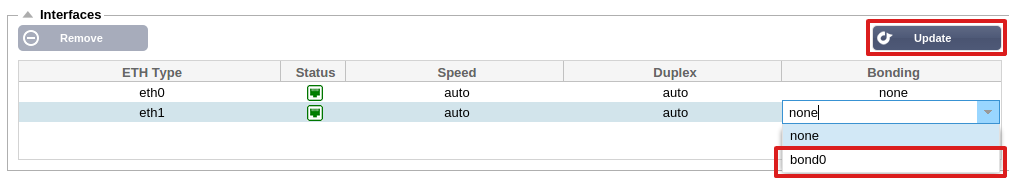
- Click on Add button on the bonding section and choose which bonding mode you wish to use
- Assign which interfaces are to be bonded in the interface section. In the example below eth0, eth1 and eth2 are now part of bond0. Whilst Eth0 remains on its own as the management interface
Adapter Status
 Adapter Up
Adapter Up
 Adapter Down
Adapter Down
 Adapter Unplugged
Adapter Unplugged
 Adapter missing
Adapter missing
IP Addressing
Now that you have added your bond you can go to the Adapter Details section to add the IP address and policy routing details
Static Route
You can manually add routes for specific subnets in this section.
Destination:
Enter the destination network address in decimal dotted notation. Example 123.123.123.5
Gateway:
Enter the gateway IPv4 address in decimal dotted notation. Example 10.4.8.1
Mask:
Enter the destination subnet mask in decimal dotted notation. Example 255.255.255.0
Adapter:
Enter the adapter that the gateway can be reached on. Example eth1.
Active:
A green tick box will indicate that the gateway can be reached. A red cross will indicate that the gateway cannot be reach on that interface. Please make sure you have set up an
interface and IP address on the same network as the gateway
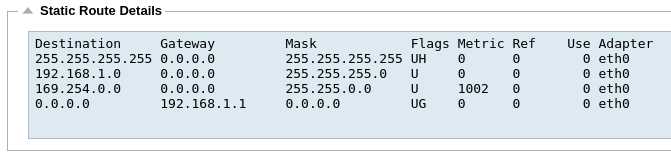
Static Route Details
This section will provide information about all of the routes configured on your ALB-X.
Advanced Network Settings
Server Nagle:
Tick this box to enable. This is a means to improve efficiency of TCP/IP networks by reducing the number of packets that need to be sent over the network. This is applied to the Server side of the transaction. Care must be taken with the server settings as nagle and delayed ack may severely impact performance.
Client Nagle:
Tick the box to enable. As above but applied to the Client side of the transaction.
The implementation and indeed definition of SNAT varies between vendors. In our case SNAT is Source Network Translation. Ie you can change the Source address of connection to something different.
Our SNAT features a strict implementation of the SNAT capabilities of the IPtables Linux firewall.
For example, the following types of rules can be easily inputted into our GUI.
## Change source addresses to 1.2.3.4.
# iptables -t nat -A POSTROUTING -o eth0 -j SNAT –to 1.2.3.4
## Change source addresses to 1.2.3.4, 1.2.3.5 or 1.2.3.6
# iptables -t nat -A POSTROUTING -o eth0 -j SNAT –to 1.2.3.4-1.2.3.6
## Change source addresses to 1.2.3.4, ports 1-1023
# iptables -t nat -A POSTROUTING -p tcp -o eth0 -j SNAT –to 1.2.3.4:1-1023
Please be careful with your rules as if they are implemented incorrectly you could create a situation where you could no longer access the device. This could result in a long drive!
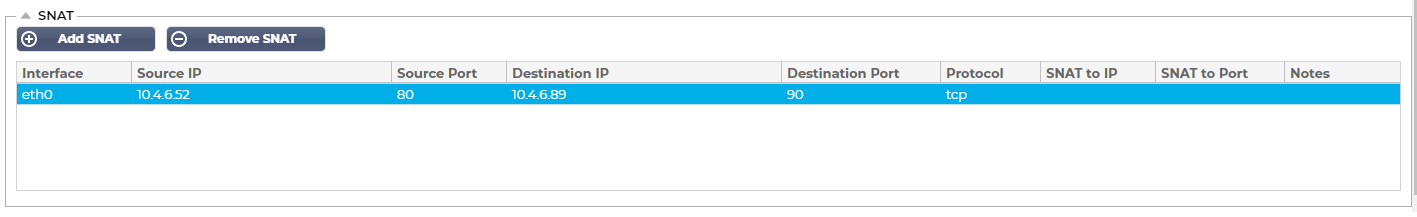
Source IP:
The Source IP address is optional, it can be either a network IP address (with /mask) or a plain IP address. The mask can be either a network mask or a plain number, specifying the number of 1’s at the left side of the network mask. Thus, a mask of /24 is equivalent to 255.255.255.0.
Destination IP:
The Destination IP address is optional, it can be either a network IP address (with /mask) or a plain IP address. The mask can be either a network mask or a plain number, specifying the number of 1’s at the left side of the network mask. Thus, a mask of /24 is equivalent to 255.255.255.0.
Source Port:
The source port is optional, it can be a single number, in which case it specifies only that port, or it can include a colon, which specifies a range of ports. Examples: 80 or 5900:5905.
Destination Port:
The destination port is optional, it can be a single number, in which case it specifies only that port, or it can include a colon, which specifies a range of ports. Examples: 80 or 5900:5905.
SNAT to IP:
SNAT to IP is a mandatory IP address or a range of IP addresses. Examples: 10.0.0.1 or 10.0.0.1-10.0.0.3.
SNAT to Port:
The SNAT to Port is optional, it can be a single number, in which case it specifies only that port, or it can include a dash, which specifies a range of ports. Examples: 80 or 5900-5905.
Notes:
Use this to put a friendly name to remind yourself why the rules exist ;-). This is also useful for debugging in the Syslog.


![]() Adapter Up
Adapter Up![]() Adapter Down
Adapter Down![]() Adapter Unplugged
Adapter Unplugged![]() Adapter missing
Adapter missing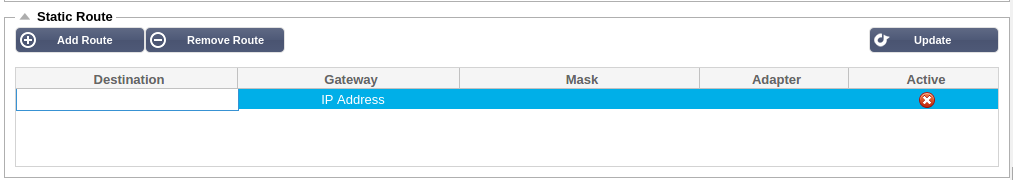


 Back to Top
Back to Top